Author: Tony Redmond
Microsoft Introduces Restore Capability for Conditional Access Policies
Restore a Conditional Access Policy Only Possible via Graph Requests For Now
Documented but not announced, the beta endpoint for the Microsoft Graph conditionalAccessPolicy resource now supports an API to restore soft-deleted conditional access policies. The restore API is used alongside the API to list soft-deleted objects used with conditional access policies. The APIs are relatively new and have not yet shown up in the Entra admin center, which currently issues a solemn warning if an administrator deletes a conditional access policy (Figure 1).

Finding Soft-deleted Conditional Access Policies
The code to discover if a tenant has any soft-deleted conditional access policies is straightforward. Because the API is relatively new, a cmdlet is not yet available in the Microsoft Graph PowerShell SDK (V2.31). No doubt a cmdlet will appear in a future version.
To discover if any soft-deleted conditional access policies exist, we execute the Invoke-MgGraphRequest cmdlet to run a HTTP request against the API and examine the details of what the API returns. The Policy.Read.ConditionalAccess permission must be available to the interactive session and the signed-in user must hold a suitable Entra role such as Conditional Access administrator or Security administrator.
$Uri = 'https://graph.microsoft.com/beta/identity/conditionalAccess/deletedItems/policies'
$Data = Invoke-MgGraphRequest -Uri $Uri -Method Get -OutputType PSObject | Select-Object -ExpandProperty Value
If ($Data) {
Write-Host ""
Write-Host ("{0} soft-deleted conditional access policies found" -f $Data.count)
Write-Host ""
$Data | Format-Table Id, displayName, createdDateTime, deletedDateTime
} Else {
Write-Host "No soft-deleted conditional access policies found to restore"
}
1 soft-deleted conditional access policies found
id displayName createdDateTime deletedDateTime
-- ----------- --------------- ---------------
14786eef-facd-41ac-83e6-19b317d3e054 Strong MFA for Hard Deletions 05/02/2025 14:05:07 02/10/2025 17:01:05
The output shows that the API found a soft-deleted conditional access policy. Like other Entra ID soft-deleted objects, conditional access policies remain in the soft-deleted state after deletion. When the retention period expires, Entra removes the policy object permanently and it is no longer recoverable.
Restore a Soft-Deleted Conditional Access Policy
Restoring a soft-deleted conditional access policy requires the Policy.ReadWrite.ConditionalAccess permission. The signed-in user must also hold a suitable RBAC role as described above. This example selects the first item in an array of soft-deleted policies returned using the first example, creates the URL to restore the policy, and executes the request to restore the soft-deleted conditional access policy. A successful restore populates the variable used to accept the output of the Invoke-MgGraphRequest cmdlet, so the code checks the variable to make sure that the restore worked:
$PolicyId = $Data[0].Id
$RestoredPolicy = $null
$Uri = ("https://graph.microsoft.com/beta/identity/conditionalAccess/deletedItems/policies/{0}/restore" -f $PolicyId)
Try {
$RestoredPolicy = Invoke-MgGraphRequest -Uri $Uri -Method Post -ErrorAction Stop
} Catch {
Write-Host ("Error restoring conditional access policy {0}" -f $PolicyId)
}
If ($RestoredPolicy) {
Write-Host ("Successfully restored soft-deleted {0} conditional access policy" -f $RestoredPolicy.displayName)
}
Another way to check that the restore worked is to run the Get-MgIdentityConditionalAccessPolicy cmdlet:
$Check = Get-MgIdentityConditionalAccessPolicy -ConditionalAccessPolicyId $RestoredPolicy.id
If ($Check) {Write-Host "Restore worked!"}
The newly restored policy will be visible in the Entra admin center the next time the Conditional Access Policies page refreshes.
Permanently Remove a Soft-Deleted Conditional Access Policy
If necessary, soft-deleted policies can be removed before the 30-day retention period expires with the delete policyDeleteItem API. Once again, the example uses the first item in an array of soft-deleted policies.
$PolicyId = $Data[0].Id
$Uri = ("https://graph.microsoft.com/beta/identity/conditionalAccess/deletedItems/policies/{0}" -f $PolicyId)
Try {
Invoke-MgGraphRequest -Uri $Uri -Method Delete -ErrorAction Stop
} Catch {
Write-Host ("Failed to remove soft-deleted policy {0}" -f $PolicyId)
}
Recovery Options are Always Good
It’s always good to have a get out of jail card that allows the recovery of items deleted in error and the new restore capabilities are a good addition to the PowerShell cmdlets for managing conditional access policies.
I’m not sure how many administrators delete conditional access policies instead of first disabling unwanted policies for a period of a week or so before proceeding to deletion. That’s still the best way of removing conditional access policies from a tenant because everything can be done through the Entra admin center. However, Microsoft has some AI-powered Entra administrative agents in preview. The current set of agents includes the conditional access optimization agent, which is designed to analyze and optimize the conditional access policies found in a tenant, including:
The agent also evaluates all existing enabled policies to propose potential consolidation of similar policies. When the agent identifies a suggestion, you can have the agent update the associated policy with one click-remediation.
If the conditional access optimization agent recommends consolidation into a smaller set of policies, it probably will result in the removal of some policies that are no longer required. Administrators click to action the agent’s recommendations. It’s good to know that if the agent proposes the removal of some policies that should be kept, at least administrators can recover the deleted policies if they go ahead with “one-click remediation.”
Insight like this doesn’t come easily. You’ve got to know the technology and understand how to look behind the scenes. Benefit from the knowledge and experience of the Office 365 for IT Pros team by subscribing to the best eBook covering Office 365 and the wider Microsoft 365 ecosystem.
Teams Stamps External Users with Trust Indicators
Trust Indicators Indicate the Level of Trust in External Users
Unfortunately, social engineering attacks designed to confuse and trick unwary users into doing something that leads to account compromise (and potentially to tenant compromise) continue unabated. According to the last number for monthly active users provided by Microsoft, 320 million people use Teams. That audience represents an attractive target for attackers to go after, and many of the social engineering attacks occur through federated chats from unknown externals users.
The original design for Teams envisaged an open collaborative environment where Teams users from Microsoft 365 domains could connect to Teams users in other domains. Attackers duly signed up trial tenants and used trial Teams licenses to reach out and attempt to connect with targets. Given that the SIP address for most Microsoft 365 users is the same as their primary SMTP address, once an attacker has an email address, they can try to institute a federated chat to that address and hope that the person at the other end responds.
Visual Clues About the Trustability of External Users
Microsoft clamped down on the ability of trial tenants to use federated chat in 2024. But attackers adapt to changed circumstances and keep on trying. This brings us to the announcement of trust indicators for Teams users published in MC1162276 (29 September 2025). Like the external tag applied to email from external sources, a trust indicator is a badge displayed alongside an external user’s name to give tenant users a visual clue about their status.
Public preview for trusted indicators has already started and is expected to be completed in late November. General availability will then roll out the feature to all tenants in all clouds for completion in early January 2026. The documentation for trust indicators describes the different badges used by Teams and where the badges appear, so I won’t go into the details here. However, here are some examples of where you’ll probably see trust indicators in action.
First, Figure 1 shows the participant list for a group chat. I’m a guest user in this chat and the badge and tooltip show that status. A guest user has a high level of trust because they are using an account added to the tenant directory to access Teams. Some might argue that this really doesn’t indicate a high level of trust because guests can be added to the tenant directory without administrative oversight. For example, by sharing a document with an external user.

Figure 2 shows another important point. In this case, we’re viewing the membership of a team and two of the members have no trust indicators. This is because they’re tenant members, so their status makes these members very trustworthy.

Build an Allow List for Teams Communications
Trust indicators are a nice addition to Teams, but I fear that they don’t address an issue that many Microsoft 365 tenants ignore, and that’s the need to control external access for Teams. I accept that it’s nice to be open and collaborative and willing to communicate with anyone in any tenant, but I also consider this to be a dangerous approach to use without question. An open tenant is an invitation to connect, but that allows unwanted visitors to attempt to connect to users.
Tenants can control the tenants that users are allowed to communicate with by establishing an external access allow list. You can build an allow list manually, but it can be difficult to know all the domains that people wish to use. It’s possible to construct the allow list programmatically with PowerShell using sources like the home domains for guest accounts or federated chats with external people. Either source is a good start for an allow list that can then be tweaked to add whatever domains are missing.
The downside of using an allow list to control Teams external access is that anytime someone wants to connect with a user in a domain that’s not in the allow list, they must seek approval for the addition of that domain. That’s regrettable, but it might be better than allowing external connections from any other Microsoft 365 domain, including those controlled by the bad guys.
Small but Important Step
Trust indicators are a small but important step to help Teams users recognize the status of external collaborators. It’s good to have these visual clues, and I hope that the clues help users to be more wary in their external communications. However, maybe it’s even better to close off the holes in Teams external access where undesirable connections can creep in.
Support the work of the Office 365 for IT Pros team by subscribing to the Office 365 for IT Pros eBook. Your support pays for the time we need to track, analyze, and document the changing world of Microsoft 365 and Office 365. Only humans contribute to our work!
Office 365 for IT Pros October 2025 Update
Monthly Update #124 for Office 365 for IT Pros Available for Download

The Office 365 for IT Pros team is delighted to announce the availability of the October 2025 update for Office 365 for IT Pros (2026 edition). This is monthly update #124. Current subscribers can download the updated EPUB and PDF files from their Gumroad.com account or by using the View content link in their receipt. See our FAQ for more information about how to download updates.
We’ve also updated the Automating Microsoft 365 with PowerShell eBook, which is now at version 16.4. The updated PowerShell EPUB and PDF files are available at the same location as the Office 365 for IT Pros book files. The paperback version of Automating Microsoft 365 with PowerShell has also been updated and is available on a print-on-demand basis from Amazon.
October Updates and the AI Effect
As usual, a bunch of changes are spread across the book chapters, details of which are in our change log. One thing that’s becoming increasingly notable is the growing percentage of Microsoft 365 message center notifications that relate to AI instead of updates to workloads like Exchange Online, SharePoint Online, and Teams.
It’s easy to understand why this is so. First, many of the Microsoft 365 workloads are very mature and already feature-rich, so less opportunity exists to add new functionality. Second, Microsoft’s development attention is obviously focused on adding as much AI-driven features to applications as possible to encourage customers to buy Microsoft 365 Copilot licenses.
The focus on AI gives us a challenge in deciding how much attention we should pay to Copilot features. We know that many Microsoft 365 tenants don’t use Copilot because the licenses are too expensive, they’ve chosen a different solution (like ChatGPT), or simply don’t see the value of AI in their environment at this point. While adding more Copilot content to the book might delight some tenants, it reduces the value of the book to other tenants.
Our current approach is to include Copilot content where it matters to tenant administration. An example is the configuration of the DLP policy to prevent Copilot Chat including content from sensitive documents in its responses. On the other hand, Copilot features that are user-centric in apps, like the facilitator agent in Teams, are usually not covered in the book. There are many of these features spread across Office and other apps. In addition, the features are in a period of rapid evolution, so documenting their use would occupy lots of time that could otherwise be used to cover topics of more general interest.
As AI becomes more embedded in administration (the initial skills available in Copilot for SharePoint Admin are a poor example of what will increasingly happen), we’ll probably change our guidelines, but that’s our current thinking.
Fixing the PDF Stamping Problem
As many of our subscribers know, Gumroad has struggled to fix a bug in the routine that stamps subscriber email addresses on our PDF files. The symptom is that the PDF is unavailable for download because it is “being prepared.” This doesn’t happen for all PDF downloads, but it happened enough to be a royal pain. Subscribers affected by the problem had to contact us, and the only workaround we had was to reissue the receipt. This action kicked off the PDF stamping routine and most of the time, it was enough to make the PDF available.
The good news is that we think Gumroad has fixed the problem by rewriting the PDF stamping routine. Every month in the recent past we have dealt with several subscribers who hit the problem. We’ll soon know if the Gumroad fix is effective. Fingers and toes are firmly crossed.
On to November 2025
As usual, we have started work on next month’s update (#125). Given that the Ignite conference is in the second half of November, there might be fewer changes to process. Then again, there’s always change in Microsoft 365, so we expect to be busy.
January 2026 Change for How Outlook Extracts Events from Email
Events from Email Only Extracted When Schema is Correct
The announcement in MC1158908 (24 September 2025) that the Outlook feature that creates events from email is going to insist that event providers must use schema.org templates to format event information from 31 January 2026 is not unexpected. Something had to change because the current implementation doesn’t work in many situations. Some events turn up in calendars, but many do not. Something had to change to restore consistency and dependability to the feature.
The Root of the Problem
Microsoft is not the root of the problem. My personal experience is that providers are radically inconsistent with respect to the information that they include about events like airline reservations and car hire bookings. The problem has become worse recently, possibly because providers treat notification emails as an extension of their corporate branding program and therefore include a bunch of information that makes the emails prettier without making sure that the essential properties for an event are available.
Microsoft says that the current method used to extract event information from email is fragile and often fails. This leads to user dissatisfaction and many support calls. Microsoft believes that their current implementation cannot be enhanced to deal with the many different ways that event providers publish information about events. They want event providers to use a standard method, and that’s where we are heading.
The Outlook Solution for Events from Email
Schema.org is an industry consortium that publishes a reference website for structured information. According to Wikipedia, the main objective of Schema.org is to standardize HTML tags that can be used to create rich results. The solution that Outlook will introduce is to insist that the HTML information about events contained in email generated by providers like airlines, car hire firms, and so on use an appropriate schema template.
For example, the flight reservation schema defines properties like provider (the airline) and reservationId (the six-character reservation identifier assigned by the airline) together with other properties like programMembershipUsed (airline frequent flyer identifier). Populating these properties properly allows Outlook to extract the details of a flight and create a calendar event with that information. Figure 1 shows an event created from details sent by Ryanair in a flight reservation email.

Up to Event Providers to Change
Apart from deciding if they want to configure the settings to instruct Outlook how to extract events from email using either OWA or the new Outlook (but not Outlook classic or Outlook mobile), users don’t have any control over event processing. A background assistant performs the processing to check inbound email and extract event details if present. It is the background assistant that will change from January 31, 2026, and refuse to process events unless the emails containing event information comply with a Schema.org template.
Whether event providers update their email to comply with the change is entirely in their hands. I’m sure that Microsoft will do some outreach with major event providers to ask those companies to support the change and they have an email address (txppro@microsoft.com) for providers who need help to upgrade to support schema.org. However, the nature of this kind of transition is that it might take some time (or even a long time) for a provider to upgrade their systems to generate event notifications in the right format.
Microsoft suggests that customers work with event providers that they use to ask those companies to comply. I guess it might be possible for a customer to ask their major suppliers (like a preferred airline) to support the change, but again, don’t expect a change to happen overnight.
Some Disruption Likely
Given the dependency on event providers to come on board and support the new way to publish event notifications, some disruption is likely to occur, and users might find that events that previously appeared automatically in their calendar no longer show up. That’s regrettable but moving to a consistent approach is a good idea and will benefit everyone in the long run. At least, that’s the plan.
Support the work of the Office 365 for IT Pros team by subscribing to the Office 365 for IT Pros eBook. Your support pays for the time we need to track, analyze, and document the changing world of Microsoft 365 and Office 365. Only humans contribute to our work!
Using the Enterprise Website Microsoft 365 Copilot Connector
Integrate External Information into Microsoft 365 Copilot Search Results
In July 2025, Microsoft released Microsoft 365 Copilot Search. On its own, Copilot Search is a great way to search SharePoint Online, OneDrive for Business, Teams, and Exchange for information available to the Graph. The more interesting aspect is the ability for tenants with Microsoft 365 Copilot licenses to integrate external sources of information into search. AS Microsoft said at the time:
“Copilot Search leverages Microsoft Graph and Microsoft 365 Copilot connectors to index content across Microsoft 365 and third-party apps. It interprets user context, natural language, behavioral signals, and organizational relationships to deliver highly personalized, context-aware answers to complex queries.”
A Gallery of Microsoft 365 Copilot Connectors
The Copilot section of the Microsoft 365 admin center includes a gallery of off-the-shelf Microsoft 365 Copilot Connectors (previously called Graph connectors). These connectors can be plugged into Copilot search by configuring them to external sources of the relevant type, like the Jira Cloud or ServiceNow (Figure 1). These are called prebuilt connectors (see the online documentation).
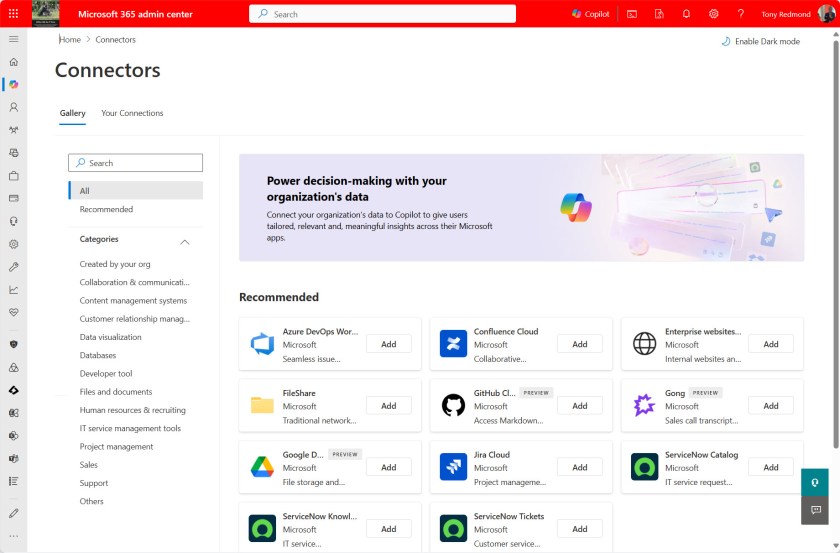
If a prebuilt connector isn’t available for your preferred source, you can develop a custom connector. For example, the People platform that Microsoft is building envisages information about people being ingested into the Graph through Microsoft 365 Copilot connectors.
Sometimes it’s hard to get your mind around whether a new feature will be valuable in your environment. If someone in your organization asked, “how can we exploit Microsoft 365 Connectors?”, my guess is that quite a few tenant administrators would struggle to come up with a cogent answer. I’d be in the same position, so decided to take a look at configuring a connector to see what happens.
Configuring the Enterprise Websites Connector
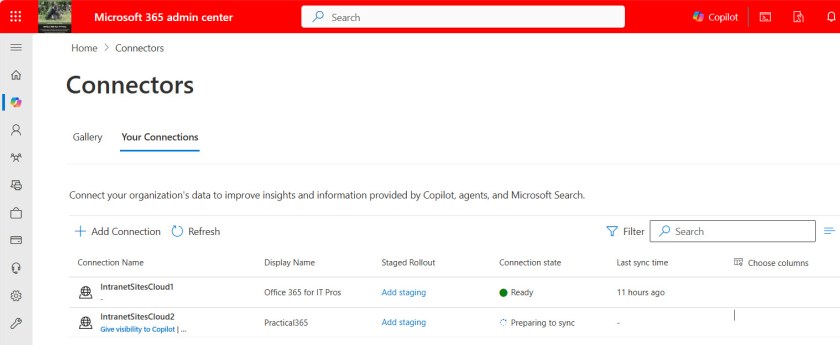
I chose to test the enterprise websites connector, which is designed to ingest material from company or public websites available on the internet. Configuring the enterprise website connector is simple. Essentially, all you need is the https URL for a website. When active, the connector crawls the target website to fetch and index content to include the material into Copilot searches. Given the superb information found in Office365itpros.com and Practical365.com, I decided to configure connectors for both sites. Figure 2 shows the configuration I used to fetch information from the Practical365.com website.

It takes some time for a connector to perform the initial crawl and bring information into Microsoft search. Eventually, the connector status will turn to Ready (Figure 3), and at that point you’ll know that the information retrieved from the website is available for searching.
Searching External Data with Microsoft 365 Copilot Search
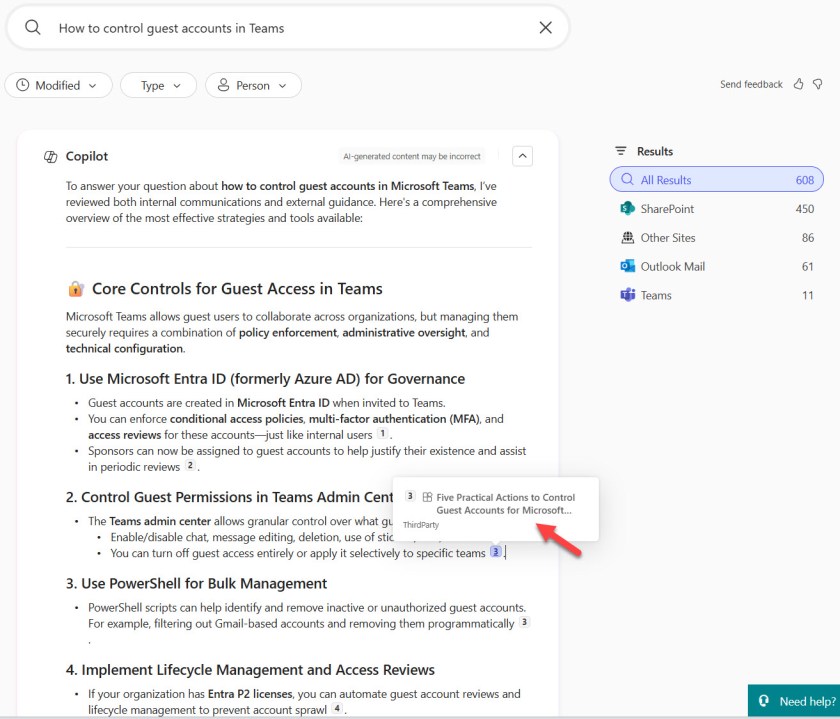
Microsoft 365 Copilot Search responds to search requests with information from all the sources available to it. I searched for information about the Microsoft 365 licensing report script that I knew occurs in articles published on Office365itpros.com (here’s one) and was rewarded with an instant hit (Figure 4) with the source that Copilot Search retrieved the information from clearly indicated in the results. Even comments for posts are indexed and available.

Clicking the link brings the user directly to the source page on the website. It’s a very seamless experience.
Even better, if asked to summarize the results, Microsoft 365 Copilot integrates the information from the external websites along with the other Graph-based information available to it. In the summary shown in Figure 5, Copilot cites a source from the Practical365.com site and tags it as “ThirdParty,” meaning that the information comes from a non-standard Graph source.
Easy, Quick, Seamless
Being able to integrate external website content into Microsoft 365 Copilot Search is one of the best features I’ve seen Microsoft launch in the blizzard of AI-related functionality introduced since the Copilot launch in March 2023. Configuring the connector is quick and easy; crawling happens automatically (and a schedule for crawling can be set up); and the results are presented seamlessly alongside items from other Graph sources. It’s a great example of the power of bringing external data into the Graph and can certainly help answer the question of what to do with Microsoft 365 Graph connectors.
Best of all, this is an easy way to integrate information from trusted external web sites into Graph searches. Who wouldn’t want to integrate content from Office365ITPros.com and Practical365.com?
Insight like this doesn’t come easily. You’ve got to know the technology and understand how to look behind the scenes. Benefit from the knowledge and experience of the Office 365 for IT Pros team by subscribing to the best eBook covering Office 365 and the wider Microsoft 365 ecosystem.
Microsoft Use of Anthropic AI Models Creates Concerns for Tenants
European Union Microsoft 365 Tenants Might Have Highest Level of Concern
On September 24, Microsoft announced an expansion of the AI models used by Microsoft 365 Copilot to include models created and maintained by Anthrophic. Initially, Microsoft says that the Anthrophic Claude Opus 4.1 model can be used with the Copilot Researcher agent, and the Claude Sonnet 4 and Claude Opus 4.1 models can be used to create agents in Copilot Studio. The Anthrophic models are not available in Copilot Chat or other Copilot integrations with Microsoft 365 apps, which continue to use the AI models.
The interesting thing about this change is that it gives Microsoft 365 tenants located in the European Union and elsewhere some issues to consider. Today, Microsoft safeguards the data used in their versions of the OpenAI models to make sure that data does not leave the tenant, compromise the EU data boundary for the Microsoft cloud, or is meets the same standards of privacy and security set down for Copilot.
Although Anthrophic seeks to reassure people about processing information in various locations, no guarantee exist about how using the Anthrophic models with Copilot Researcher or to create Copilot agents maintains the same level of enterprise data protection and integrity that Microsoft has emphasized to date for its AI systems and highlights for the Copilot Researcher agent (Figure 1).

Microsoft Documents the Compliance and Processing Risk
Microsoft’s documentation covering how to connect to the Anthrophic models emphasizes that:
When your organization chooses to use an Anthropic model, your organization is choosing to share your data with Anthropic to power the features. This data is processed outside all Microsoft‑managed environments and audit controls, therefore Microsoft’s customer agreements, including the Product Terms and Data Processing Addendum do not apply. In addition, Microsoft’s data‑residency commitments, audit and compliance requirements, service level agreements, and Customer Copyright Commitment do not apply to your use of Anthropic services. Instead, use of Anthropic’s services is governed by Anthropic’s Commercial Terms of Service and Anthropic’s Data Processing Addendum.
In other words, all bets are off once a tenant goes off the beaten path to explore the glorious uplands of the Anthrophic models. The flat warning given by Microsoft that data will be processed outside the Microsoft environment without any audit controls is stark. It makes other administrative challenges like stopping individual users from uploading files to ChatGPT for processing seem very simple (because uploads are easily blocked).
The loss of all the Microsoft Purview compliance functionality built up around Copilot like the interaction audit records captured by the Microsoft 365 substrate is a big problem. It’s certainly enough to stop all but a few tenants that have a clearly defined and well understood need to use the Anthrophic models from venturing down the path to choose Anthrophic in the Copilot section of the Microsoft 365 admin center (Figure 2).

Where Next?
Choice is always good and Microsoft’s move to expand the pool of available Large Language Models is a worthwhile initiative. Although the targets for the Anthrophic models are currently limited, the guardrails around the use of those models are also limited. Considering the effort expended by Microsoft to develop security and compliance controls for Copilot since the March 2023 launch, it seems that there’s a huge amount of work to be done before third-party models become a serious option for many Microsoft 365 tenants, even in limited circumstances.
The work to bring model choice to Copilot is obviously evolving, and no doubt Microsoft will deliver some of the controls desired by customers over time. Quite how many of the Purview controls can be applied to third-party AI processing remains an open question.
Support the work of the Office 365 for IT Pros team by subscribing to the Office 365 for IT Pros eBook. Your support pays for the time we need to track, analyze, and document the changing world of Microsoft 365 and Office 365. Only humans contribute to our work!
SharePoint Knowledge Agent Available in Preview
Knowledge Agent to Sort Out SharePoint Metadata
With all the associated hype that’s now the norm for a Microsoft announcement associated with AI, the SharePoint development group launched the preview of the SharePoint Knowledge Agent on September 18, 2025. You think “so what” because SharePoint has supported agents for almost a year. However, those agents reason over the content of files found in a site while the big difference with the Knowledge Agent is that it deals with site metadata and its purpose is to make sites work better rather than to help users find information.
Given Microsoft’s promise that the new agent could help stream content management (aka, sort out the mess that’s in so many sites) to “SharePoint into a dynamic, intelligent knowledge hub that gives your organization a competitive edge,” it seemed like a good thing to test. That is, if you have a Microsoft 365 Copilot license.
Enabling a Microsoft 365 Tenant for the SharePoint Knowledge Agent
With the licensing issue out of the way, the next step is to enable the tenant to support the Knowledge Agent. This can be done for all or selected sites, as described in the documentation. Enabling Knowledge Agent can only be done through PowerShell at this point, and throwing caution to the breeze, I elected for all sites and ran this command after connecting to SharePoint Online:
Set-SPOTenant -KnowledgeAgentScope AllSites
Using the SharePoint Knowledge Agent
There’s no point in testing any software against just a few objects, so I started by testing the Knowledge Agent against a site containing roughly 4,000 files in 10.2 GB of storage. The Knowledge Agent has its own floating action menu, which appears on top of the regular document view (Figure 1).

Given my notorious lack of organization, the Organize this library option seemed like a good place to start. The options (Figure 2) include creating three columns to hold metadata that the agent will generate to make the library easier for Microsoft 365 Copilot to process, creating a rule to do something when an action happens in the library, extract key actions from files to populate an autofill column, and summarize files.

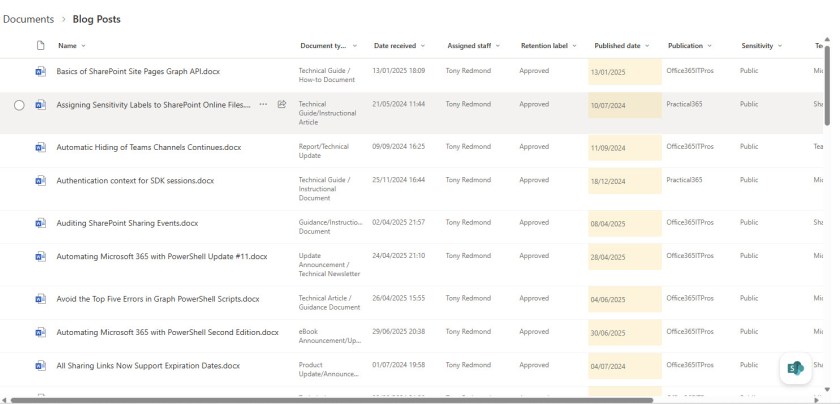
I asked the Knowledge Agent to create some suitable columns. The document library already has some custom columns that I use to organize and search articles that I’ve written. As such, you might think that the library is already well-organized. The agent thought for a bit and then suggested that the library could use columns for the document type, date received, and assigned staff. If you agree, the agent adds the new columns to the existing view or creates a new view that includes the columns.
The important thing is that these are autofill columns. SharePoint auto-fills the properties for new files when they are created, and to backfill the properties for older files, background processes use the Copilot LLMs to generate the necessary information (Figure 3). The backfill process doesn’t happen immediately, and full population of the columns for all items can take a few days. The categorization of articles into document type was the most interesting part of the exercise, but nothing was gained from the date received (date the item was uploaded to SharePoint) and assigned staff (always me) columns.
The extract key actions and summarize options also use autofill columns to hold their results. The summaries are like the automatic summaries created by Copilot for Word documents. There’s no indication of if or how often the agent checks files for new or changed text to update the metadata and the autofill status doesn’t provide too much insight into what’s happening. Mostly, the autofill status showed information about processing that occurred over eight hours ago even when it was obvious that the agent had processed files more recently. In Figure 4, the agent updated the summary (for this article) but the autofill activity page lagged way behind.

Obviously, if the agent can’t extract text to summarize, it cannot populate these columns, so expect good results from Office and PDF files and lesser joy elsewhere. The agent experienced some problems with Word documents translated into Japanese by the SharePoint translation service, but on the upside, the agent stripped text nicely out of JPEG files to report what it found there.
Creating a rule calls the standard SharePoint feature, so there’s not much to say about it except that the agent possibly makes it a little easier for people to create rules. However, if they want to make changes to the rule, they’ll still need to go to SharePoint’s Automate menu, select Rules, and then Manage rules.
No Audit Records for Agent Processing
Unlike when humans create SharePoint agents, there’s no trace of Knowledge Agent activity in the audit log. This is perhaps unsurprising because the creation of SharePoint agents is only auditable by checking FileUploaded audit events for .agent files. Other workloads, including Exchange Online, create audit records when background processes perform actions that affect users, so I don’t know why SharePoint Online lags in this respect.
No Real Magic
The Knowledge Agent is a preview and who knows what the final version will deliver. For now, I find little trace of any magic generated by AI in what the Knowledge Agent delivers. But it’s entirely possible that my testing did not cover the kind of scenarios that Microsoft envisages the agent delivering most value, like classifying legal documents, or to help HR organize the resumes for job applicants.
I would have liked to try the agent out on sites with different types of information, but even though the Knowledge Agent is enabled for all sites, its action menu is only available in the first site I chose for testing (the situation persists a week after enabling the Knowledge Agent). There’s got to be something simple that’s going wrong here, but I can’t find an answer to the case of the missing action menu.
Insight like this doesn’t come easily. You’ve got to know the technology and understand how to look behind the scenes. Benefit from the knowledge and experience of the Office 365 for IT Pros team by subscribing to the best eBook covering Office 365 and the wider Microsoft 365 ecosystem.
Assembly Clashes Make Microsoft 365 PowerShell Frustrating
Assembly Clashes Happen too Often
In June, I reported a problem with V3.8 of the Exchange Online management PowerShell module when called by Azure Automation runbooks. The problem was caused by the removal of .NET6 support in the Exchange Online module, which meant that runbooks using the PowerShell V7.1 or V7.2 runtime engines couldn’t load. The Microsoft Graph PowerShell SDK did the same thing with the same effect, proving that developers don’t look much outside their own software to discover how problems might occur when software dependencies change.
The Authentication Assembly Dependency
Complex software often has some form of dependency. In the case above, it was the version of .NET that caused problems. New .NET versions appear and have a support schedule, so it’s understandable that software products should move to the latest supported version and want to discard versions that are no longer supported. What’s not understandable is when engineers make changes with no regard to what might happen to customer production scripts.
But an even more irritating problem that continues to happen is Microsoft’s failure to sort out the use of .NET assemblies across important PowerShell modules like the Microsoft Graph PowerShell SDK, Exchange Online management, and Microsoft Teams.
All the modules need to authenticate connections, so they call the Microsoft Authentication Library (MSAL) and load the Microsoft.Identity.Client assembly to allow clients to authenticate. An assembly is a building block for .NET applications. In this instance, the MSAL assembly contains the code necessary to allow an application (like a PowerShell module) to authenticate with Entra ID and obtain the necessary access tokens to work with data.
Connecting with Exchange and then the Graph
Sometimes the Microsoft 365 PowerShell modules fail to use the same version of the assembly, which means that an older version can be loaded into a session and cause a problem for a module loaded afterwards. Take this example using V3.9 of the Exchange Online management module and V2.30 of the Microsoft Graph PowerShell SDK:
PowerShell 7.5.3 Connect-Exchangeonline -showBanner:$false Connect-MgGraph -NoWelcome Connect-MgGraph: InteractiveBrowserCredential authentication failed: Method not found: '!0 Microsoft.Identity.Client.BaseAbstractApplicationBuilder`1.WithLogging(Microsoft.IdentityModel.Abstractions.IIdentityLogger, Boolean)'.
Connect-ExchangeOnline runs first and authenticates, so the MSAL assembly it requires is loaded into the session. When Connect-MgGraph runs, it checks for a method that doesn’t exist in the loaded MSAL assembly and barfs. Microsoft’s support guidance for the Microsoft Graph PowerShell SDK recommends using the latest bits, but this problem happened with the latest available release.
The problem goes away if Connect-MgGraph is run before Connect-ExchangeOnline. When this happens, the Graph has the assembly it needs and the Exchange module is happy to use the later version of MSAL.
A Known Problem for Years
Assembly clashing between PowerShell modules has been a known problem for years. A recent issue posted to GitHub notes that Microsoft does not implement assembly loading properly because all assemblies are loaded globally (and so affect all modules loaded into the session) rather than in an application context (just for one module).
The mismatch of MSAL assemblies has been an issue for quite a while (here’s a similar problem report from August 2023). To be fair to Exchange Online, the Azure Accounts module has also experienced assembly clashing with the Microsoft Graph PowerShell SDK.
To be fair to the Microsoft Graph PowerShell SDK, assembly clashing is known between Exchange Online and Microsoft Teams. Figure 1 shows what happens when you attempt to run the Connect-MicrosoftTeams cmdlet (V7.3.1) after running Connect-ExchangeOnline:

It’s kind of weird that Connect-MicrosoftTeams isn’t recognized as a cmdlet. Everything works perfectly when Connect-MicrosoftTeams runs before Connect-ExchangeOnline.
No Change Without Consensus
Assembly clashes will continue until the Microsoft engineering groups coordinate development better to ensure common usage of important .NET assemblies. It doesn’t take much to communicate what version of an assembly a module needs so that everyone can reach consensus on the version modules use. Maybe Copilot could help. In the interim, the only solution is to make sure that the order scripts load modules doesn’t cause a problem, and to repeat that check after each release of important modules.
Updating the User Password and Authentication Report
Change to Beta Graph API Requires Update to User Password and Authentication Report Script
Last year, I wrote about how to exploit the newly-added Graph API to report the per-user MFA state for Entra ID accounts. As with all additions to the Graph, the new API used the beta endpoint, which is where APIs function when Microsoft is happy to expose the API in public while still knowing that some work is needed before the API can advance to the production (V1.0) endpoint.
Recently, a reader posted a comment about the article and said that when they ran the script in their tenant, no data showed up in the “Default MFA method” column in the report. I write scripts to illustrate principals and explore what’s possible rather than attempting to create production-ready code. In addition, it’s impossible for me to see what’s happening in another tenant, unless the tenant administrator gives me the necessary account with permissions, and that shouldn’t happen. My default response is therefore to ask people who report issues to do some basic PowerShell debugging by selecting the code where the problem seems to lie and running the commands to see what happens. Besides, I was on vacation, so I didn’t want to spend any time looking into what the issue might be.
Searching for the Problem
To cut a long story short, the person who reported the problem responded with sufficient data to indicate that an issue was present. After returning from vacation, it was time to open Visual Studio Code (and GitHub Copilot) and try to figure out what was happening.
The code looked good, and nothing seemed out of the ordinary. The script used Graph requests rather than cmdlets from the Microsoft Graph PowerShell SDK, but that’s a normal state with newly-released beta APIs because the AutoRest tool that generates SDK cmdlets from the API metadata hasn’t yet included the cmdlets in an SDK release. To make the code easier to read, I replaced a couple of API requests with SDK cmdlets and then noticed that the output from the Get-MgBetaUserAuthenticationRequirement cmdlet no longer contained details of a user’s default MFA method. This was the cause of the problem.
The Downside of Beta Graph APIs
Using beta APIs (or beta cmdlets) is a double-edged sword. The positive is access to functionality sooner than waiting for Microsoft to upgrade an API to a production release. Some APIs stay in the beta endpoint for years, and you can’t predict when Microsoft might consider an API to be reliable, robust, and performant enough to justify promotion from beta to production.
The downside is that beta features are prone to change based on developer and customer feedback, the need to accommodate changes elsewhere in the underlying workload, or as the side effects of bug fixing or tuning for performance. I have no idea why Microsoft removed the default MFA method output from the data reported by the cmdlet. Maybe it was because the UserPreferredMethodForSecondaryAuthentication property contains similar information.
A New User Password and Authentication Report Script
In any case, my script can only report what’s available, so I updated the code to remove the obsolete column and renamed the UserPreferredMethodForSecondaryAuthentication column to be “Preferred MFA method” (Figure 1). The change seemed to make sense at the time. If you disagree, feel free to create a GitHub push request to update the script. I’m happy to review any and all suggestions.

Don’t Depend on Beta Graph APIs
All of this goes to show that developers who rely on beta Graph APIs need to keep a wary eye out for changes that might impact their code. The change can happen at any time and probably won’t be flagged by Microsoft because it is, after all, a change to a beta API that’s expressly not intended for production use. I should learn my lesson (some day). In the meantime, enjoy the updated user password and authentication report script and all the other examples in the Office365itpros GitHub repository. I’m sure there’s a few more bugs lurking there that I need to attend to.
Need some assistance to write and manage PowerShell scripts for Microsoft 365, including Azure Automation runbooks? Get a copy of the Automating Microsoft 365 with PowerShell eBook, available standalone or as part of the Office 365 for IT Pros eBook bundle.
Automating Microsoft 365 with PowerShell October 2025 Update
Version 16 of Automating Microsoft 365 with PowerShell Available for Download

The Office 365 for IT Pros team is proud to announce the October 2025 update for the Automating Microsoft 365 with PowerShell eBook. The book is available separately and as part of the Office 365 for IT Pros eBook bundle. Current subscribers can download the latest files from their Gumroad.com account. See our FAQ for more information about how to download the updated EPUB and PDF files.
The October 2025 update for Office 365 for IT Pros is under development and should be available for download on October 1, 2025. Subscribers can check their account then or wait until they see the update notification posted here.
Current Files are Version 16.2
At the time of writing, the current files are labelled version 16.3 and dated 22 September 2025. I originally created version 16.0 to use as the basis for the paperback version so that I could get some printed copies to take with me to The Experts Conference (TEC) in Minneapolis (September 30-October 1). TEC features a PowerShell script-off where conference participants sign up to compete against others to solve common Microsoft 365 administrative problems, and I wanted printed copies to give to the script-off competitors.
Alas, the best laid plans sometimes come a cropper, and I found changes that I wanted to get into this month’s update not once but twice, which resulted in the 16.1, 16,2, and 16.3 versions. However, the delay involved in print on demand means that the books that will show up at TEC are version 16.0. When you get used to being able to update and publish a book update electronically, reverting to waiting for printing presses to run seems very antiquated, even in a print on demand scenario. Tant pis, or so the French might say.
Exchange SE for Administrators
In other news, Scott Schnoll, who left Microsoft earlier this year, has published The Admin’s Guide to Microsoft Exchange Server Subscription Edition. The book is available from Amazon.com (paperback and Kindle) for a whopping list price of $119.99 (currently available at a discounted $90.07 for the paperback and $99.99 for Kindle) and promises “never before heard details on the development of Exchange Server Subscription Edition.”
There’s no doubt that some confusion exists around Exchange SE, especially in terms of licensing (this FAQ helps), but that’s probably a symptom of the move to subscriptions. To facilitate the changeover, Microsoft made sure that 99.99% of the technical detail for Exchange SE is the same as for Exchange 2019. This position will change as Microsoft adds new functionality to Exchange SE over time.
Whether a new book about existing technology with a high price point will succeed remains to be seen. Amazon takes a large chunk (up to 70%) of the price paid by buyers and that might have dictated the price for a book that targets a declining (but still important) market.
The nice thing about writing about on-premises server products is that authors don’t have to cope with the rapid pace of change experienced in the cloud. However, the details and features of Exchange SE will diverge from Exchange 2019 from this point, so change will come. That change probably won’t be unduly dramatic and Exchange SE will not become like Exchange Online, so the work to keep the book updated shouldn’t be too onerous.
For any self-published book about technology, I recommend using a site like gumroad.com (which we use for Office 365 for IT Pros) or leanpub.com (home of Paul Thurrott’s Windows 11 Field Guide and other great books). Both sites offer authors more revenue for book sales and better control over changes, which is always nice. On the other hand, Amazon offers a decent on-demand paperback printing service that we use for the paperback version of the Automating Microsoft 365 with PowerShell book. You pay your money and make your choice…
On to Version 17
We continue to develop content for Automating Microsoft 365 with PowerShell based on changes and updates to PowerShell modules. I can’t predict what the next month will bring. I can only say that things will happen that will turn up in version 17.
Copilot Chat Arrives in Microsoft 365 Apps
A Logical Progression for Copilot in the Microsoft 365 Apps
The news in message center notification MC1096218 (last updated 17 September 2025) about the rollout of Copilot Chat confirms the worst fears of some that Microsoft is on a one-way path to stuffing Copilot into as many places as it can. Well, that feeling is backed by some truth, but in this case, I think the change is a natural progression of Copilot’s existing presence in apps like Word, where it’s been producing document summaries since last year.
Once Copilot appeared in the Office apps, there was only one way forward, and that wasn’t to see Copilot disappear from Office. Now Copilot Chat is available in Word, Excel, and PowerPoint, just like it has been available in Outlook (new and classic) for a while. Microsoft says that the rollout is expected to complete in the coming weeks, which basically means that it will turn up when the stars align in terms of desktop client Office build and server infrastructure.
Copilot Chat for All
Copilot Chat is available for any user of the Microsoft 365 apps, with or without a Microsoft 365 Copilot license. The difference is that those with Microsoft 365 Copilot licenses can access tenant resources like documents stored in SharePoint Online and OneDrive for Business while those without are restricted to web queries (via Bing search).
Working in Copilot and an Office App
The idea behind the side-by-side implementation is that users can work on a file in the main pane while being able to interact with Copilot in a side pane (Figure 1). It’s a useful feature that makes it easy to take questions from the main file, research them in Copilot, and take the results back into the file.

Apart from anything else, integrating Copilot so tightly into the Office apps makes it less likely that users will seek AI assistance elsewhere and potentially end up uploading documents from SharePoint and OneDrive to services like ChatGPT. It also encourages people to consider upgrading from the free Microsoft Copilot to the full-feature and more expensive Microsoft 365 Copilot.
Word Action Button for Microsoft 365 Copilot Chat
After Outlook, Word is easily the Office app where I spend most time. The announcement in message center notification MC1143298 (last updated 17 September 2025) that an Open in Word action button will soon be available to move text from Copilot to Word is therefore very interesting.
It’s possible to move content from Copilot to Word now using Copilot pages as an interim step. Copilot pages are built from Loop, so the intention is that the content is worked on in Loop after coming from Copilot rather than being exported to a new app. At this point, Word is a more sophisticated word processing tool than Loop is. Given the use cases for the two apps, this is the natural state of affairs. I seldom need to collaborate with others to write articles or book text. Being able to move content from Copilot to Word is an action I shall check out once it becomes available later this month.
Teams Move to the Unified Microsoft 365 Apps Domain
Before closing for the weekend, a little bird tells me that Teams might soon move from its teams.microsoft.com domain to teams.cloud.microsoft as part of the initiative launched by Microsoft to create a unified domain for Microsoft 365 apps.
In March 2024, Microsoft posted a note for developers to tell them that Teams apps needed to be able to use teams.cloud.microsoft. By this point, I’m sure that most ISVs will have updated their apps, but if your tenant has some custom home-grown Teams apps, it’s worthwhile checking with the developers that the apps are ready to accommodate the domain switch. Who wants to be surprised when the switch happens?
Support the work of the Office 365 for IT Pros team by subscribing to the Office 365 for IT Pros eBook. Your support pays for the time we need to track, analyze, and document the changing world of Microsoft 365 and Office 365. Only humans contribute to our work!
What’s the Best Way to Manage Guest Accounts?
Home-Brewed PowerShell or Microsoft Solutions for Guest Account Management
A recent podcast from the genial Merill Fernando featured Microsoft’s Jeremy Conley to talk about “how to really govern guest access.” The tagline “many tenants have 2-4x more guests than employees” captures the focus of the episode (a good listen) and while many organizations might not believe that guest accounts are quite so numerous in their Microsoft 365 tenants, the simple fact is that it’s all too easy to accumulate a vast collection of guests.
Microsoft 365 is responsible for this sad state of affairs. I started talking about the problems of guest accounts “going bad” (aging) soon after the introduction of Azure AD guest accounts for Office 365 groups in 2016 and the situation hasn’t improved much since. Things really took off with the introduction of Teams in 2017 and later, the adoption of guest accounts by SharePoint Online as the basis for sharing. My basic recommendation has always been to review guest accounts annually with the aim of removing unused guests.
Use Entra Governance or PowerShell for Guest Account Management
Microsoft has solutions to help, but only if organizations invest in Entra P2 licenses (naturally) to liberate ID governance features like lifecycle management and access reviews. If you can afford the licenses, you should certainly investigate using lifecycle management and access reviews to control guest accounts. But you don’t need to spend any money on additional licenses because controlling guest accounts is a reasonably straightforward task using PowerShell. Let’s discuss some of the tactics that tenants could adopt for guest management.
First, Microsoft doesn’t implement an expiration date for guest accounts, but this is easily done by assigning an expiration date to guest accounts and using that date as the basis for checking if guest accounts are still needed.
For any type of guest account management, it’s a good idea to review guest sign-in activity. If a guest account doesn’t sign into a tenant within a certain period (say, 90 days), it’s probably obsolete and can be removed.
Entra ID supports the concepts of account sponsorship. In other words, one or more sponsor accounts can be associated with member or guest accounts. Sponsors are not assigned by default, but setting a default sponsor is easily done for guest accounts. The problem with default sponsors is that the selected account might not have any insight into how a guest account is used, but a default sponsor is better than none, and the lack of activity should always be the primary reason for considering an account to be inactive and a candidate for removal.

Sponsors are supposed to know why an account exists, so if a guest account is deemed obsolete due to lack of sign-in activity, you can report this fact and use the report data to contact the sponsors to ask if accounts should be removed or kept.
The Need to Nag Sponsors
One thing I haven’t done yet is to send nagging email to account sponsors to say that their sponsored guest accounts will be automatically removed in a week or so if they don’t reply with a justification for keeping the accounts. This is a good example of where a scheduled Azure Automation runbook is a good choice to run the code to check for obsolete guest accounts and email the account sponsors. I must write that script!
No one wants to remove guest accounts that are required for business purposes. Teams is probably the best example of where important guest accounts that appear underused might exist. I’ve documented five practical actions to manage guest accounts used with Teams topic in this article. Enforcing multifactor authentication for guest accounts through a conditional access policy is a critical step.
Act to Make Sure Your Tenant Implements Guest Account Management
Whether you decide to manage guest accounts using your own code or with Microsoft’s solutions really doesn’t matter. The important thing is to manage guest accounts, especially in terms of a regular clean-out of obsolete accounts. Insisting on multifactor authentication removes most of any security risk associated with having some underused guest accounts in Entra ID, but who doesn’t like a clean directory?
Need some assistance to write and manage PowerShell scripts for Microsoft 365, including Azure Automation runbooks? Get a copy of the Automating Microsoft 365 with PowerShell eBook, available standalone or as part of the Office 365 for IT Pros eBook bundle.
Entra ID’s Keep Me Signed In Feature – Good or Bad?
Should Microsoft 365 Tenants Disable Keep Me Signed In?
When I wrote about the Entra ID Keep Me Signed In (KMSI) feature in February 2022, I concluded that growing threats might have made the feature less valuable than it once was. Like anything to do with Microsoft 365, the passing of time requires re-evaluation of attitudes and opinions, and this is true for KMSI too. Here’s my best attempt at summarizing the current state of the art.
Recapping How the Keep Me Signed In Feature Works
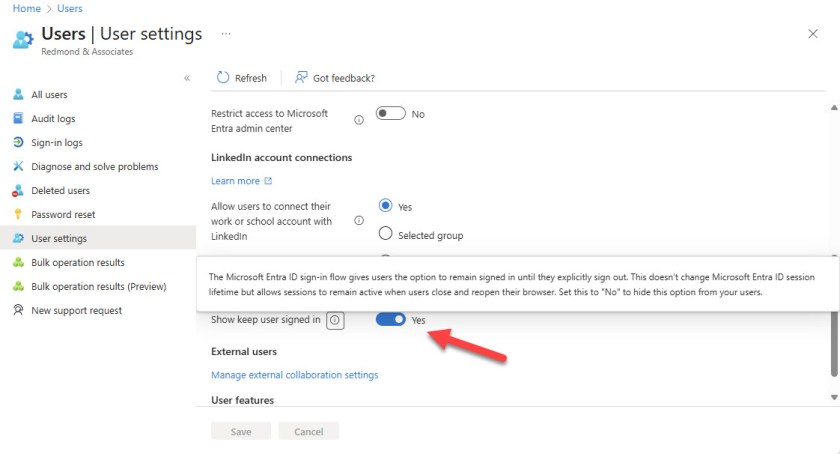
As a recap, KMSI is the option presented to users after they authenticate to “stay signed in” to reduce the number of times Entra ID forces the user to sign in. If the user chooses to stay signed in by choosing the Yes option (Figure 1), Entra ID creates a persistent authentication cookie that can last for up to 90 days (as opposed to 24 hours, which is the lifetime of a non-persistent cookie). With a persistent autentication cookie available, the user can connect to applications without signing in for the lifetime of the cookie. Because the cookie is persistent, it doesn’t matter if the browser session is restarted.

The Don’t show this again checkbox has nothing to do with the creation of the persistent authentication cookie. The checkbox controls whether Entra displays the prompt on the device for future sign-ins.
Obviously, a persistent authentication cookie is a bad idea if workstations are shared, but when workstations are personal and only used by a single person, keep me signed in is a nice way to reduce the friction of signing in. In fact, the Entra ID sign-in flow contains some logic to detect if a sign-in originates from a shared device and won’t show the stay signed in screen in this case. The same is true if Entra ID considers a sign-on to be high risk.
Clearing browser cookies on a workstation will remove the persistent authentication cookie.
Conditional Policies and Sign-in Frequency
Conditional access policies can interfere with the operation of persistent authentication cookies. If a conditional access policy insists that users reauthenticate based on a certain frequency, the full authentication process is invoked, and users must provide credentials. Some tenants impose unreasonable demands on users (or just guest accounts) and insist on very frequent authentication, so it’s a matter of achieving balance between annoying users and maintaining the desired level of security.
Considering the Question of Enabling Keep Me Signed In
All of which brings me back to the question of whether Microsoft 365 tenants should enable or disable KMSI. Generally speaking, I don’t see anything wrong with KMSI when the following conditions are true:
- People use personal rather than shared workstations. Authentication processing for people who use shared workstations can be controlled by specific conditional access policies.
- Strong multi-factor authentication is in place to ensure that the initial authentication is secure and is unlikely to be compromised by external attackers. In other words, use the Microsoft authenticator app or passkeys.
- Conditional access policies are in place to impose a reasonable sign-in frequency. Monthly seems about right. After using a weekly frequency for the last few years (for one tenant that I access frequently as a guest), I think this interval creates too much friction.
As always, the first order of business is to prevent user accounts being compromised. If an account is not compromised, KMSI is unlikely to cause a problem. The widespread adoption of continuous access evaluation by Microsoft 365 workloads makes closing off compromised account access easier, but that’s no excuse to avoid deploying strong multifactor authentication everywhere to protect every Microsoft 365 account.
Configuring Keep Me Signed In
To configure KMSI for everyone in a tenant, use the checkbox in User settings in the Entra admin center (Figure 2). KMSI is either enabled or disabled. It can’t be enabled for a specific group of users and disabled for everyone else.
KMSI is Fine in the Right Conditions
Microsoft 365 users have enough on their plate to cope with the ongoing and constant change in the apps they use daily. Reducing friction from sign-ins through features like KMSI seems like a good idea, providing it can be done securely and doesn’t compromise the tenant. Deploying strong multifactor authentication and effective conditional access policies go a long way to establishing the right conditions for KMSI. But if your tenant is open to compromise because it still uses single factor authentication (passwords) or lets people use weak multifactor authentication methods, don’t blame KMSI when you are compromised. At that point, persistent authentication cookies are the least of your worries.
So much change, all the time. It’s a challenge to stay abreast of all the updates Microsoft makes across the Microsoft 365 ecosystem. Subscribe to the Office 365 for IT Pros eBook to receive insights updated monthly into what happens within Microsoft 365, why it happens, and what new features and capabilities mean for your tenant.
Copilot Administrative Skills Don’t Do Much for SharePoint Management
SharePoint Skills in Copilot Won’t Impress SharePoint Administrators
Message Center notification MC1147976 (4 September 2025, Microsoft 365 roadmap item 501427) apparently heralds a new era of AI-enhanced administrative assistance for Microsoft 365 workloads. The post describes two skills to assist administrators in the SharePoint Admin Center:
- Step-by-step task guidance: Copilot provides clear instructions to help administrators complete common tasks.
- Multi-variable site search: Copilot enables administrators to search for sites using multiple conditions, such as inactivity, external sharing, and size, and suggests recommended actions.
The change will roll out in general availability worldwide from October 6, 2025. The capability showed up in my targeted release tenant, so I thought that I’d ask Copilot to help me to manage SharePoint Online, especially because of the promise that Copilot will help “both new and experienced admins complete tasks faster.” Alas, the skills exhibited by Copilot didn’t live up to expectations.
SharePoint Skills and the Promise of AI
Largely because of Teams, SharePoint Online administrators have many more sites to manage than in the past. It therefore makes perfect sense to apply artificial intelligence to help administrators detect potential problems that might be lurking or to find sites that need attention.
I started by asking Copilot to find which sites have most files. That seems like a pretty simple question for AI to answer, but it’s not and Copilot couldn’t answer, saying that it was unable to search for that criterion (Figure 1).

Hmmm… Such a response seems at odds with Microsoft’s promise that Copilot will strengthen governance at scale by allowing administrators to “ask complex questions and receive actionable results, making it easier to detect risks and enforce lifecycle policies across large environments.” Knowing which sites store most files seems like a fundamental piece of information from a data lifecycle perspective.
SharePoint Skills Need Data
The root of the problem is likely to be the data available for Copilot to reason over. All the Microsoft 365 admin centers present sets of data relevant to a workload through their UX. The Exchange admin center deals with mailboxes and other mail-enabled objects; the Entra admin center deals with directory objects; the Teams admin center deals with Teams policies and other team-related information, and so on. The information in these data sets is whatever’s accessible through and presented by the admin centers.
In the case of my question, the SharePoint Online admin center doesn’t have the data to respond because there’s nowhere in its UX that surfaces the file count for sites. In fact, although the SharePoint admin center reports the total number of files in the tenant, finding the file count for a site takes some effort unless you use the slightly outdated information that’s available through the site usage Graph API.
On the other hand, when I asked Copilot to “Find sites without a sensitivity label that have more than 1GB of storage,” the AI could respond because the storage used by each site is available in the SharePoint admin center (Figure 2).

Delivering the Promise
Tenant administrators have a lot to do, so any tool that can help is welcome. This is a first-run implementation, so it’s bound to have flaws. Copilot can offer limited help that novice administrators might welcome while not offering much to anyone with some experience. Microsoft is likely to iterate its Copilot assistance for SharePoint administrators to improve, deepen, and enhance what Copilot can offer, but I fear it will take several attempts before the promise of AI is delivered.
What SharePoint Skills Would Help Administrators?
This raises the question of what kind of assistance Microsoft 365 administrators might want AI tools incorporated into the admin centers to deliver? To me, the answer lies in bringing information together from available sources to answer questions faster than a human being can.
For example, SharePoint advanced management includes a change history report. It would be nice if an administrator could ask Copilot to review all changes made to SharePoint over the last month to report changes like sensitivity label updates for any site that generate label mismatches for documents. The information is available in audit logs and SharePoint document libraries, but it takes effort to bring everything together in a concise and understandable format. AI should be capable of answering questions like this instead of simple queries against site properties, which is all that Copilot can do today, and that is hardly a great example of AI in action.
Insight like this doesn’t come easily. You’ve got to know the technology and understand how to look behind the scenes. Benefit from the knowledge and experience of the Office 365 for IT Pros team by subscribing to the best eBook covering Office 365 and the wider Microsoft 365 ecosystem.
Copilot Transcription Behavior Changing for Teams Meetings
Default Changes to Copilot Enabled Without Transcription
First issued on August 22, 2025, and updated on September 5 to clarify the timeline, message center notification MC1139493 (Microsoft 365 roadmap item 478611) flags an important change in how Microsoft 365 Copilot functions in Teams meetings. Ever since the introduction of Copilot, the way things worked is that transcription is enabled when Copilot is used in meetings. After Microsoft rolls out the change starting in early November 2025, using Copilot in Teams meetings will no longer enable and save transcripts. This change might be disruptive if meeting organizers expect transcripts to be available after meetings conclude, but as always, the devil is in the detail and this change might not affect your tenant.
The change isn’t surprising given that Copilot can answer meeting participant queries without a transcript (this wasn’t originally the case) and that Microsoft has gradually tightened access control to the meeting transcript over time.
Why Change the Generation of Meeting Transcripts
Microsoft isn’t saying why Copilot-enabled Teams meetings will no longer generate a transcript, but it’s probably to safeguard against the possibility that Copilot will regurgitate meeting discussions in its response to user prompts.
Meeting transcripts are stored in the meeting organizer’s OneDrive for Business account and are indexed by Microsoft Search. Because their content is indexed, transcripts are available for Copilot to process just like any other document that isn’t blocked by the DLP policy for Microsoft 365 Copilot. Meeting organizers with Teams Premium licenses can apply a sensitivity label to files shared during a meeting, but the sensitivity label doesn’t apply to the transcript.
Will The Change Affect My Tenant
The simple answer is yes, if your tenant uses the default Teams meeting policy. That’s because Microsoft manages the settings of default Teams policies and can adjust policy settings as needed.
In this instance, Microsoft will change the value of the Copilot setting in the Teams meeting policy from EnabledWithTranscript to Enabled. The first value is in place today and it’s what instructs Teams to generate the transcript with Copilot. The second value allows Copilot to be used in Teams meetings without the generation of a transcript. If you check the documentation for the Set-CsTeamsMeetingPolicy cmdlet, you’ll see that Microsoft refers to a “persisted” and “non-persisted” transcript. A persisted transcript is one that’s saved to OneDrive for Business; a non-persisted transcript is one that Teams generates internally to allow Copilot to reference what people have said during the meeting before deleting all trace of the transcript when the meeting finishes.
New Microsoft 365 tenants will automatically pick up the Teams meeting policy default settings. Existing Microsoft 365 tenants will use the default settings for new meetings.
An exception exists where custom meeting policies are in use. It’s relatively common to customize Teams policies and the meeting policy is often changed to meet organizational needs. When a tenant customizes a default policy, Teams copies the default policy to create a custom copy for the tenant. The tenant controls the settings of custom policies and Microsoft therefore cannot change the default setting for Copilot. In other words, everything happens as before and enabling Copilot for a meeting will generate and save a transcript.
If Microsoft updates meeting policies for a tenant, it’s easy to revert the change to ensure that transcription occurs with Copilot. The change must be made with PowerShell by running the Connect-MicrosoftTeams cmdlet to connect to Teams PowerShell. Then, run this code to find which meeting policies have Copilot enabled without a transcript:
Get-CsTeamsMeetingPolicy | Where-Object {$_.Copilot -eq "Enabled"} | Format-Table Identity To update a policy and restore Copilot with transcription, note the policy name and update it like this:
Set-CsTeamsMeetingPolicy -Identity "RestrictedFunctionality"-Copilot "EnabledWithTranscript" -AllowTranscription $true
Copilot Transcription for Individual Meetings
Even if Microsoft updates the default Teams meeting policy, meeting organizers can opt for transcription through meeting options either when scheduling (Figure 1) or during the meeting.

Persistent Conversations in Meetings
In MC1139493, Microsoft also make the point that conversation history has been made persistent within meetings. In other words, participants can switch between different elements of a meeting like chat or viewing the participant list without losing access to Copilot insights, even without a transcript being taken. The point is that when transcription is not enabled, persistence is possible using the internal transcript, which is how it should be.
So much change, all the time. It’s a challenge to stay abreast of all the updates Microsoft makes across the Microsoft 365 ecosystem. Subscribe to the Office 365 for IT Pros eBook to receive insights updated monthly into what happens within Microsoft 365, why it happens, and what new features and capabilities mean for your tenant.
Running Teams PowerShell Cmdlets in Azure Automation
Why Would You Need to Run Teams PowerShell Cmdlets in an Azure Automation Runbook
The new permissions requirement for Entra ID apps that want to use cmdlets from the Teams PowerShell module creates the question of what conditions could occur to make apps need to use the Teams cmdlets. After all, access to Teams structures and data is available through Graph APIs and the Microsoft Graph PowerShell SDK. The answer lies in the history of the policy-drive management framework used by Teams.
When Microsoft launched Teams in 2017, they borrowed from many existing technologies. Teams took its approach to management from Skype for Business Online and adapted many of the policies used by Skype for Business to control how meetings, messaging, and other aspects of the system worked. This decision made a lot of sense as it became clear that Teams would replace Skype for Business Online, a decision first revealed in September 2017 and eventually completed in July, 2021.
The Teams PowerShell module appeared in late 2017. I didn’t like the module very much at the time, but have become accustomed to it over time as Microsoft removed the rough edges. One such irritation was the Skype for Business connector, the component used to allow PowerShell control over Teams management policies. In February 2021, Microsoft retired the Skype for Business connector and moved its cmdlets into the Teams module. The legacy of the Skype connector cmdlets still exists today with cmdlets like Get-CsOnlineUser and Get-CsTeamsMeetingPolicy.
In general, any cmdlet with a “Team” prefix (like Get-TeamChannel) is Graph-based and an equivalent cmdlet is in the Microsoft Graph PowerShell SDK (Get-MgTeamChannel in this instance). Any cmdlet with a “Cs” prefix (like Get-CsTeamsMessagingPolicy) uses the old Skype for Business framework and doesn’t have a Graph SDK equivalent. It’s therefore a reasonable conclusion that Entra ID apps need to use the Teams PowerShell module only when apps need to interact with Teams policies. The Graph handles Entra ID app access to teams, channels, chats, meetings, and so on.
Running Teams PowerShell in Azure Automation
Running PowerShell in Azure Automation runbooks is like running PowerShell through Entra ID apps. Both need to be authentication before cmdlets run, and both need some permissions to access data. Permissions can be granted explicitly or via membership of a management role.
Unless the need exists to do widespread and extensive policy reassignment to accounts, I’m not sure that many runbooks use Teams PowerShell. The exception might be where a tenant develops a script based on Teams PowerShell and wants to run the script on a scheduled basis, or the script takes so long to run that interactive execution becomes a pain. In these cases, Azure Automation is a good answer, especially because the Connect-MicrosoftTeams cmdlet supports managed identities for authentication.
The caveat is that some of the cmdlets in the Teams PowerShell module are unsupported when application-based authentication is used. New-Team is the most notable cmdlet in this category, but that gap is easily worked around by creating a new team through Microsoft Graph PowerShell SDK cmdlets.
Configuring Azure Automation for Teams PowerShell
Temas uses much of the setup used to run other Microsoft 365 PowerShell modules with Azure Automation. An automation account must be available that’s connected to an Azure subscription. Ideally, the automation account should support managed identities. The module must be loaded as a resource into the runtime environment. Teams PowerShell supports the PowerShell V7.4 runtime engine, so a custom runtime environment can be used.
Before attempting to authenticate, the service principal for the automation account must be assigned:
- The Teams administrator role. This is what allows the automation account to run the cmdlets in the module as a Teams administrator. The role can be assigned with PowerShell or via the Entra admin center (Figure 1).
- Any Graph API application permissions needed to access the Teams data processed by runbooks. For instance, because Teams management might be gated by administrative units, the RoleManagement.Read.Directory and GroupMember.Read.All permissions are needed to read details about administrative units and the members of those units. Other Graph permissions like Chat.Read.All might be needed to read information stored in teams.

With these preprequisites in place, you should be able to create and execute runbooks using the Teams PowerShell module. Figure 2 shows the output from a very simple runbook that connects to Teams with a managed identity before listing the teams in a tenant.

Not the Normal Option
My normal course of action is to use the Microsoft Graph PowerShell SDK or Graph API requests to interact with Teams (like reporting details about Teams online meetings or analyzing chat messages with external users to figure out an allow list for external access) and I seldom use the Teams PowerShell module with Azure Automation. However, the option is there if needed, and that’s good to know.
Need some assistance to write and manage PowerShell scripts for Microsoft 365, including Azure Automation runbooks? Get a copy of the Automating Microsoft 365 with PowerShell eBook, available standalone or as part of the Office 365 for IT Pros eBook bundle.
Running the SharePoint Site Content and Policy Comparison Report
Use the SharePoint Site Content Report to Highlight Issues – If You Can Find Any
As quickly as they can and in as many ways as possible, Microsoft is attempting to address the problem of digital rot in SharePoint Online. Having old, obsolete, inaccurate, and just plain wrong information in SharePoint Online and OneDrive for Business doesn’t matter so much until the eagle eye of AI tools are deployed. At that point, all manner of misleading responses can appear because the AI is grounded on misleading or incorrect information.
To some extent, customers cannot be blamed for the digital debris that they accrue in SharePoint Online. For years, Microsoft has encouraged cloud storage (the latest tactic is a policy setting to block users from saving to non-cloud locations), so it’s natural that some rot accumulates along with valuable material. As I’ve said before, many of the problems customers have encountered with Microsoft 365 Copilot deployments are the legacy of previous Microsoft collaboration strategies. Not everyone goes through the process of auditing the files stored in SharePoint Online to remove dross (here’s how to create a report of files in a document library, and here’s how to do the same for a OneDrive for Business account).
The Site Content and Policy Comparison Report
All of which brings me to the “SharePoint AI-powered site content and policy comparison report” announced in MC1143287 (27 August 2025). The report is available to tenants with Microsoft 365 Copilot or SharePoint Advanced Management (SAM) licenses. It’s one of the SAM features made available to Copilot customers without the need for SAM licenses. The site content and policy comparison report is rolling out in general availability now with completion worldwide due in late December 2025.
According to Microsoft, the idea is that a tenant selects a reference site that they regard as a good example of a site with “up-to-date and relevant policies” to use as a benchmark to compare up to 10,000 other sites against (Figure 1). In addition to policies that apply to the site (like data lifecycle policies), the reference site should contain more than 10 files of the same kind of material that’s found in the target sites. This is because the comparison uses the 10 most recently used files from each site.

The report uses AI to examine the target sites. The target sites can be chosen by uploading a CSV containing their URLs or selected using several site properties, ranging from the simplest (examine everything as shown in Figure 2) to identifying sites based on the container management sensitivity label assigned to sites, the site type, creation date (for example, sites created within the last 30 days), sites with no owners, and sites where external sharing is disabled.

Nothing in My Reports
Behind the scenes, AI compares the target sites against the reference site to highlight inconsistent application of policies based on the similarity between the reference site and target sites (here’s the documentation). After pondering on any anomalies that it finds (a process that Microsoft warns could take up to 48 hours), the AI generates a report for administrators to consider and potentially act upon.
And that’s where my story ends because despite multiple attempts to select a good reference site to compare against the other sites in my tenant, the AI always came up with an empty report. I even purposely populated a site with content that I knew is similar to other sites and edited ten of the files added to the site to make sure that fresh material was available for the comparison. The site had the same sensitivity label and settings as the reference site, but the report still ignored it.
Maybe my SharePoint Deployment Has No Problems
I could take a positive view and conclude that the AI discovered no irregularities. For instance, all my team sites have container management labels and have assigned retention policies. It could also be the case that the selected reference sites are very dissimilar to the other sites in the organization, so much so that none of the other sites came close enough to be of interest.
However, I suspect that the AI comparison just doesn’t work well for tenants where many similar sites exist but only a few of those sites are actively used. I also wonder why Microsoft insists on comparing the last ten most recently used files because if the intention is to help organizations prepare for Copilot, then perhaps sites that hold many files without having sufficient recently modified files should be highlighted? After all, in the eyes of AI tools, a file is a file, and the information contained in a file that hasn’t been modified in years could end up being cited in a Copilot response. Using old material often leads to poor responses.
Don’t assume that just because it didn’t work for me, the site content and policy comparison report is rubbish. It might work well in your tenant and highlight many areas that you should investigate to improve the tenant readiness for AI.
Learn about managing SharePoint Online and the rest of Microsoft 365 by subscribing to the Office 365 for IT Pros eBook. Use our experience to understand what’s important and how best to protect your tenant.
Microsoft’s Effort to Develop a Broad People Platform
Build Out of a Complete Person Platform within Microsoft 365
After publishing the article about customizing the Microsoft 365 profile card through the Microsoft 365 admin center, I started to think about the work Microsoft is doing on the “people platform,” an effort to unify the different strands of people-related data that exist inside Microsoft 365, such as Entra ID, mailbox properties, skills defined for SharePoint Online users (now the people skills solution), people settings like name pronunciation and personal pronouns, and so on. Drawing together disparate sources of information to create a unified view of a person (tenant user, guest, or contact) seems like a good idea, especially if AI tools like Copilot use people information to enhance responses to user prompts.
Exploiting the Graph to Discover More About the People Platform
I’ve often argued that acquiring a knowledge of how the Microsoft Graph works and how to interact with Graph APIs is a good way to gain an insight into how Microsoft 365 works. In this case, the profile resource type is very revealing. A lot of the work in this area is still in beta and is therefore prone to change, but you can see where Microsoft is heading in the description of the Microsoft 365 person experience (described for a multi-geo tenant, but still valid):
“The Microsoft 365 Person encompasses the complete set of properties, attributes and associated people contacts that are representative of a user in the Microsoft 365 tenant.”
The sources used to build the complete picture of a person include:
- Basic administrative information about people stored in Entra ID, including information synchronized from on-premises Active Directory. This information includes the display name, employee identification number, employee type, physical location, and so on. It also includes the person’s photo.
- Data to build out the one-dimensional picture of a user as found in Entra ID by populating information about the person’s jobs (work positions or roles), skills, languages, education (including certifications), and so on. This information can be added programmatically through the Graph APIs or imported from an external system using a Copilot connector for people data.
Adding a Work Position
To demonstrate what kind of information the people platform uses to build out a complete picture about a user, I spent a little time playing with the Microsoft Graph PowerShell SDK cmdlets that add work position information to the people platform. A work position is a job or role undertaken by a person within a business. The role might be in the past or current, so a complete work history within an organization can be constructed from the work position data. Like the rest of the platform, these cmdlets are based on beta code, so some stuff doesn’t work. Nevertheless, the information defined for a work position is a good example of what Microsoft is doing.
This code adds a new work position, marking the role as current (isCurrent is true). The allowedAudiences property is set to organization, meaning that the information is available within the organization (it could also be set to “me,” meaning that it’s personal to the user). After building the properties to describe the role, running the New-MgBetaUserProfilePosition cmdlet adds the work position record to the people platform. This is equivalent to posting a request to the https://graph.microsoft.com/beta/users/{userId}/profile/positions endpoint.
$AddDate = ([datetime]::UtcNow.ToString("s")) + "Z"
[string]$AddDate = '2025-09-04T22:18:03.8608268Z'
[string]$endDate = '2039-09-04T22:18:03.8608268Z'
$Parameters = @{}
$RoleDetail = @{}
$RoleDetail.Add("jobTitle", "Senior Technical Manager")
$RoleDetail.Add("role", "Technology Consulting")
$RoleDetail.Add("employeeId", "150847")
$RoleDetail.Add("employeeType", "Permanent")
$RoleDetail.Add("description", "Responsible for the management of a small team of technical consultants covering the NYC area")
$RoleDetail.Add("level", "MGR-02")
$RoleDetail.Add("startMonthYear",$AddDate)
$RoleDetail.Add("endMonthYear", $EndDate)
$Company = @{}
$Company.Add("displayName", "Office 365 for IT Pros")
$Company.Add("department", "Consulting")
$Company.Add("officeLocation", "New York City")
$Company.Add("costCenter", "100014")
$Company.Add("division", "Professional Services")
$Company.Add("webUrl", "https://office365itpros.com/")
$Address = @{}
$Address.add("type", "business")
$Address.add("street", "170 Avenue of the Americas")
$Address.add("city", "New York City, New York")
$Address.add("countryOrRegion", "United States")
$Address.add("postalCode", "10036")
$Company.Add("address", $address)
$RoleDetail.Add("company", $Company)
$Parameters.Add("detail", $RoleDetail)
$Parameters.Add("isCurrent", "true")
$Parameters.Add("allowedAudiences","organization")
$Parameters.Add("createdBy", "Tony Redmond")
New-MgBetaUserProfilePosition -UserId $User.Id -BodyParameter $Parameters
After positions are added, the Get-MgBetaUserProfilePosition cmdlet can retrieve an array of all the work positions known for the user:
[array]$Positions = Get-MgBetaUserProfilePosition -UserId $User.Id
The information written by New-MgBetaUserProfilePosition is available in several composite properties, like Detail (Figure 1). It’s easy to see how this information might surface on a form of the current profile card.

You’ll always find a position registered for a user because the people platform synchronizes details from Entra ID to create a default position from information like a user’s job title held in the directory.
A Complex Undertaking
It’s obvious that building the people platform is a complex undertaking. Anything to do with personal information is sensitive. Personal privacy must be protected. I am sure that employee unions and worker councils will take a keen interest in how Microsoft 365 tenants decide to populate the Graph with people information and then, more importantly, how that data surfaces in places like the Microsoft 365 profile card.
It’s often said that we live in interesting times. Things might just get more interesting as the people platform develops. It’s certainly something that anyone involved in identities and user management should keep an eye on.
Insight like this doesn’t come easily. You’ve got to know the technology and understand how to look behind the scenes. Benefit from the knowledge and experience of the Office 365 for IT Pros team by subscribing to the best eBook covering Office 365 and the wider Microsoft 365 ecosystem.
Microsoft’s Push to Save Office Files in the Cloud
New Policy Setting to Force Office to Save to Cloud Locations
Announced in Microsoft 365 message notification MC1137593 on 18 August 2025, Microsoft is introducing a new policy setting to force the creation (saving) of Office files in cloud locations. The setting only applies to Word, Excel, and PowerPoint files saved using the Microsoft 365 enterprise apps (subscription version of Office). No other Office version is affected.
Cloud locations means SharePoint Online, OneDrive for Business, and third-party cloud storage services like Dropbox or ShareFile (if the feature is enabled for the Microsoft 365 tenant).
The new policy enablecloudonlysaveasmode setting can be deployed to clients using Group policies or registry updates. The setting is available in the Administrative Template files for Microsoft Office (version 5516.1000 or newer) and applies to the Windows versions of the Microsoft 365 enterprise apps version 2506 (build 19029.2000) or later. I checked the feature using version 2508 (build 19127.20192) (Current Channel Preview).
MC1137593 says that public preview started to roll out in late August 2025 and is scheduled to complete by mid-September 2025. General availability for all clouds will start in mid-September 2025 and should be available everywhere by the end of September 2025. If you don’t take steps to apply the policy setting, nothing changes.
Higher Cloud Usage
Microsoft says that the new policy is “part of a new set of tools for IT Administrators to move their organizations towards higher Cloud usage and Increase security and compliance.” Increasing cloud usage adds stickiness to the Microsoft cloud because the more data that users store in SharePoint Online and OneDrive for Business, the harder it is to move to any other platform.
The point about increasing security and compliance is justified by the fact that SharePoint Online and OneDrive for Business are subject to the tenant’s security and compliance policies. It’s true that cloud files are more resilient than files stored on a local drive and it is very convenient to be able to move from PC to PC while keeping files available. However, everything depends on the network and if the network’s not available or you don’t want to use a potentially insecure network like free wi-fi, losing the ability to save files to the local drive can be a real pain. I often save copies of Offices files as PDFs to share with other people, and I don’t really want those PDFs cluttering up OneDrive.
Microsoft sometimes goes overboard in its enthusiasm to save files in OneDrive, like PowerShell modules. Some might consider this step to be in that category.
What Users See
The default situation is shown in Figure 1. No policy is configured, and the user can save to SharePoint Online, OneDrive for Business, the local hard drive, and other cloud services (configured through Add a Place).

With the policy setting enabled, Office applications are limited to cloud locations to save new files or save existing files as a new file (Figure 2). Note that the “This PC” and “Browse” (for folder) options are missing.

Updating Office with the Microsoft 365 Apps Policy
Microsoft 365 tenants can apply the setting to restrict saving to the cloud via a cloud policy configured in the Microsoft 365 Apps center. Search for the Restrict saving on non-cloud locations setting and change the value from not configured to enabled (Figure 3).

After saving the policy, its settings are applied by the click to run service and the new setting should be active within a day.
Like most Office settings, the change can be made manually by updating the system registry on a PC. In this case, it seems like the setting is controlled by two settings. The first enables the cloud only save mode by creating a new DWORD value called EnableCloudOnlySaveAsMode at HKEY_CURRENT_USERSOFTWAREMicrosoftOffice16.0CommonFileIO. The second apparently removes the UI options for non-cloud locations through another DWORD value called PreferCloudSaveLocations at HKEY_CURRENT_USERSoftwareMicrosoftOffice16.0CommonGeneral. Both values are set to 1 to enable or 0 to disable. When I tested, the settings worked on one PC and not on another. It took too long to figure out that the PC where things worked ran Current Channel (Preview) while the one where the feature didn’t work ran Current Channel.
A Change That Might Annoy Some
Some will hate this change and ask what’s the point of having a local drive if it’s inaccessible. Others might not notice that all files are stored in the cloud because they do that as the norm. And some will only notice the change when they go to save a file locally. I save most of what I do with Word, Excel, and PowerPoint in the cloud, so I guess that I’m in the last category.
If I was forced to live with storing all Office files in the cloud, I could adapt my workflow without much difficulty. Until a network outage occurs…

Support the work of the Office 365 for IT Pros team by subscribing to the Office 365 for IT Pros eBook. Your support pays for the time we need to track, analyze, and document the changing world of Microsoft 365 and Office 365. Only humans contribute to our work!
Microsoft Bolts on Copilot License Check onto ExRCA
Hard to Find Logic for Copilot License Check in Exchange Connectivity Tool
Unless you’re a keen reader of the Microsoft blogs posted to the Microsoft Technical community, you might have missed the August 25 article about a new diagnostic tool for a “Copilot License Details Check.” According to the text, it’s “a powerful tool designed to streamline and validate your license readiness by confirming whether Copilot for Microsoft 365 licenses are properly assigned to users.” In reality, it’s some Graph API requests cobbled together to report details of a Microsoft 365 Copilot license assignment to a user account that’s been bolted onto the side of the Exchange Remote Connectivity Analyzer (ExRCA).
As I explain in another article, ExRCA started as a troubleshooting tool to help Exchange on-premises administrators debug connectivity problems with protocols like Autodiscover and ActiveSync (check out the YouTube video from that time). Later, Microsoft upgraded ExRCA to support Exchange Online and Teams. At this point, it’s fair to say that ExRCA is an invaluable tool for Microsoft 365 tenant administrators.
However, having a valuable support tool is no reason to bolt on a license checker. I’m sure Microsoft will point to the inclusion of the message header analyzer tool in ExRCA as evidence that ExRCA has become a toolbox, but that’s missing the point that the message header tool is at least associated with a messaging protocol (SMTP) whereas the Copilot license check is a barefaced attempt to help people use more Copilot features.
Running a Copilot License Check
Running a Copilot license check is very simple. Input the user principal name or primary SMTP address of a user account, sign in as an administrator with permissions to access user account details, and the code runs to verify that the account has a Microsoft 365 Copilot license with all its service plans intact (Figure 1).

A Simple Check
Stripping everything away, the license check is very simple and the results that it generates are equally simple (no expensive CPU cycles for AI analysis are burned here). Figure 2 shows that the user being checked is good to go. I’m sure that this is deemed to be a successful test.

But some issues exist. First, the test doesn’t distinguish between direct-assigned licenses and group-assigned licenses, which is valuable information for an administrator to know if they want to address a problem highlighted by the test. Second, the test only considers a “full” Microsoft 365 Copilot license to be valid. Trial licenses are not considered valid. Third, disabling some Copilot features is a perfectly reasonable thing to do. Not everyone needs to create new agents through Copilot Studio, for example.
PowerShell Code for the Copilot License Check
To show what the ExRCA Copilot check does, I recreated the check using the Microsoft Graph PowerShell SDK. The code is simple and took about an hour to write (including testing):
- Sign into the Graph with Connect-MgGraph using an administrator account.
- Prompt for a user account and validate that the account exists.
- Check that the account has a valid Microsoft 365 Copilot license (including trial licenses). License and service plan information is available online.
- Run the Get-MgUserLicenseDetail cmdlet to retrieve service plan information for the Copilot SKU.
- Check each of the service plans defined in the license to report if it is enabled or disabled.
Figure 3 shows some sample output.

You can download the script from the Office 365 for IT Pros GitHub repository.
No Reason to Use ExRCA to Check License Details
I don’t know how many Microsoft 365 tenant administrators will seek out ExRCA to answer questions like “I wonder if the Copilot license assigned to John Doe is good to go?” It seems like an unnatural reaction to consider ExRCA in that light when it’s straightforward to build your own tools to measure user readiness for Copilot or analyze and report licenses assigned to user accounts (including disabled service plans).
The idea might be a good one, but I fear it’s implemented in the wrong place and is too limited to deliver much value.
Need some assistance to write and manage PowerShell scripts for Microsoft 365, including Azure Automation runbooks? Get a copy of the Automating Microsoft 365 with PowerShell eBook, available standalone or as part of the Office 365 for IT Pros eBook bundle.










